Protect your sensitive data and adjust data flow in your company.
In Protection, you can define what should happen when Safetica NXT comes across any info being transferred.
By creating your own policies, you can modify the risk of selected events and enforce restrictions. You can explicitly state whether you consider an event dangerous or not, and what action to take on the device when an incident happens.
Some destination types have limited support on macOS devices. You can find the details here.
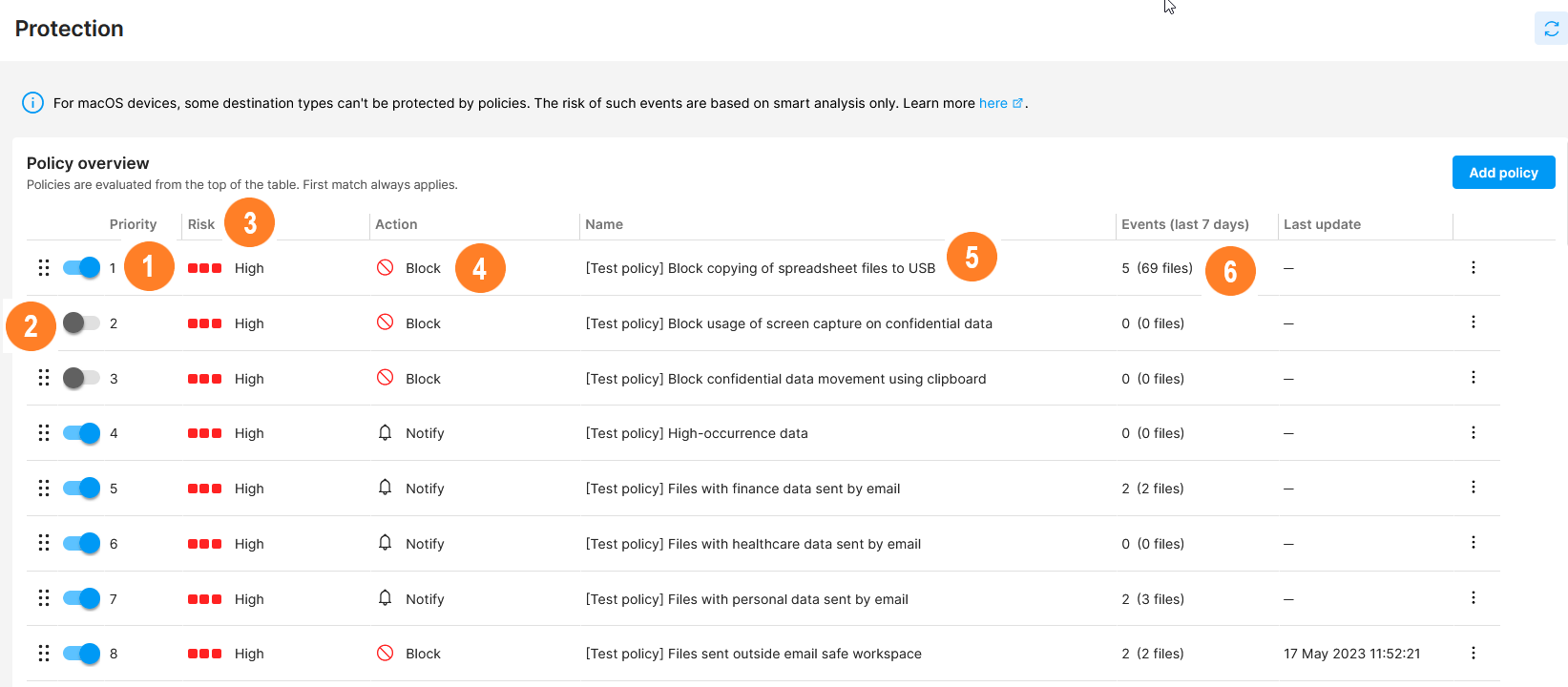
In the list of policies, you can see:
![]() The priority each policy has. Since policies are evaluated from the top to bottom of the policy list, the priority of each policy is vital during evaluation.
The priority each policy has. Since policies are evaluated from the top to bottom of the policy list, the priority of each policy is vital during evaluation.
You can change policy priority by drag-and-dropping them to their correct position.
![]() The state of the policy, which can be either Enabled or Disabled.
The state of the policy, which can be either Enabled or Disabled.
Disabled policies are skipped during evaluation.
![]() What risk will be assigned to events that violate the policy (you can choose between High and None).
What risk will be assigned to events that violate the policy (you can choose between High and None).
![]() What action will be taken on the device where the policy was violated, i.e. how the policy will affect the device. The event can be logged, blocked, or the user can be notified and decide whether to finish the action or not.
What action will be taken on the device where the policy was violated, i.e. how the policy will affect the device. The event can be logged, blocked, or the user can be notified and decide whether to finish the action or not.
![]() The name of the policy - click it to display policy detail.
The name of the policy - click it to display policy detail.
There are several predefined policies (their names start with [Test policy]) that help you start protecting your environment right after Safetica installation.
![]() The number of events that matched a particular policy in the last 7 days. Click the number to see more details about the events in Data security.
The number of events that matched a particular policy in the last 7 days. Click the number to see more details about the events in Data security.
How policies work in Safetica NXT
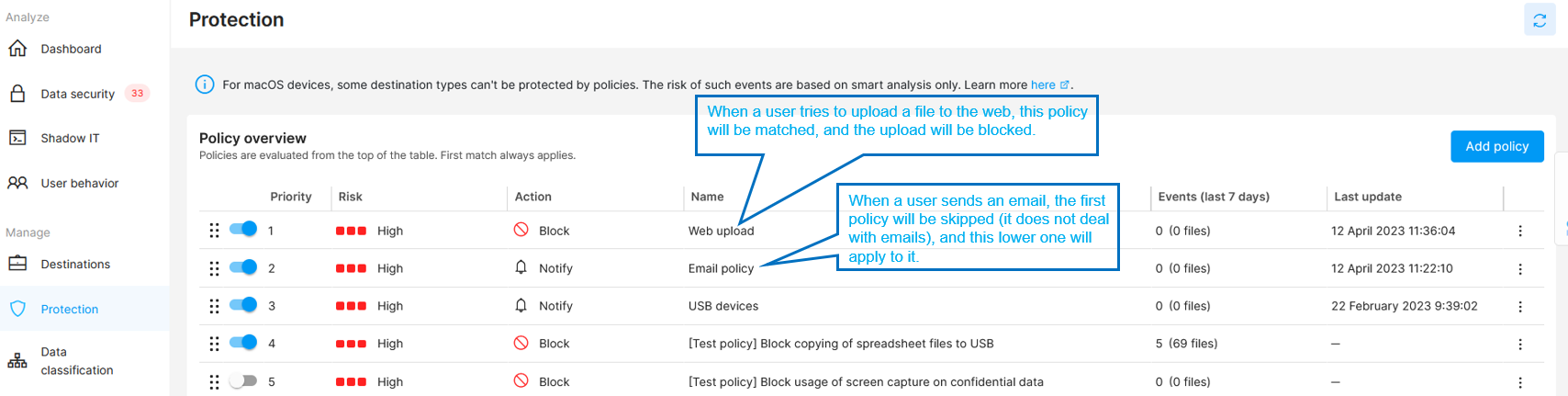
Policies in Safetica NXT are prioritized ![]() and evaluated from the top to the bottom of the policy list.
and evaluated from the top to the bottom of the policy list.
- First match always applies.
- If a policy is matched, the policy action is performed.
- Each policy has several sections (e.g. destination types or teams), which are evaluated separately.
- A policy is matched when ALL its sections are matched (AND relationship).
- If no match is found for a policy, the evaluation continues with lower-priority policies until a matching policy is found.
- If no matching policy is found, no action is taken.
A new policy is always placed to the top of the policy list. You can then prioritize it by drag-and-dropping it to its correct position.
We recommend placing general policies and policies with no risk at the bottom of the table. More specific policies, policies with high risk, and exceptions should be placed at the top.
Example: When a policy is found with a first-match rule for upload, the action assigned to that rule will be performed, and upload will not be evaluated any further. Evaluation will continue, however, for other operations (e.g. for email). These will be evaluated by policies placed lower in the list until a first match is found.
Policy disclaimer
Compatible web browsers, email clients, instant messengers, remote transfer apps, and cloud are supported here.
A comparison of features supported on macOS and Windows devices is listed here.